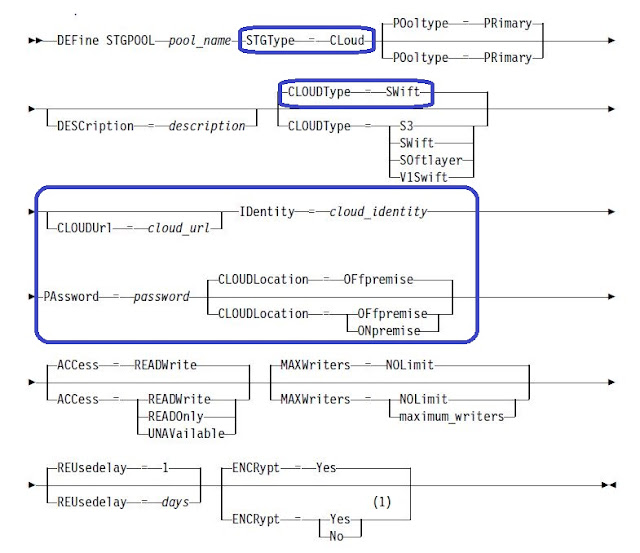
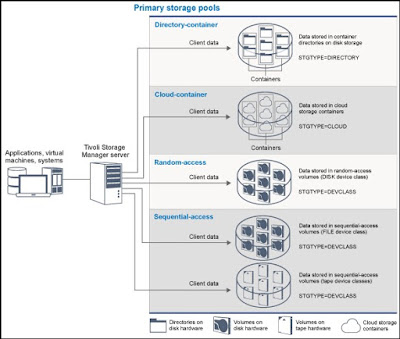
Starting from Tivoli Storage Manager Version 7.1.3, you can use the new storage pool type called directory-container storagepool to protect backup and archive data. Data that is stored in a directory-container storage pool can use either inline data deduplication, client-side data deduplication, inline compression, or client-side compression. Tivoli Storage Manager offers the following features when you use directory-container storage pools for data storage
- You can apply data deduplication and disk caching techniques to maximize data storage usage.
- You can retrieve data from disk much faster than you can retrieve data from tape storage.
Inline data deduplication or inline compression reduces data at the time it is stored. By using directory-container storage pools, you remove the need for volume reclamation, which improves server performance and reduces the cost of hardware. You can protect and repair data in directory-container storage pools at the level of the storage pool by using AUDIT CONTAINER command.
- Simplified storage management.
- Optimized data-deduplication processing.
- Reduced database growth and size.
- Increased server performance and scalability.
- Improved recoverability of damaged extents
Some TSM internal process does not support for directory-container storage pools. You cannot use any of the following functions with directory-container storage pools:
- Migration
- Reclamation
- Aggregation
- Collocation
- Simultaneous-write
- Storage pool backup
- Virtual volumes
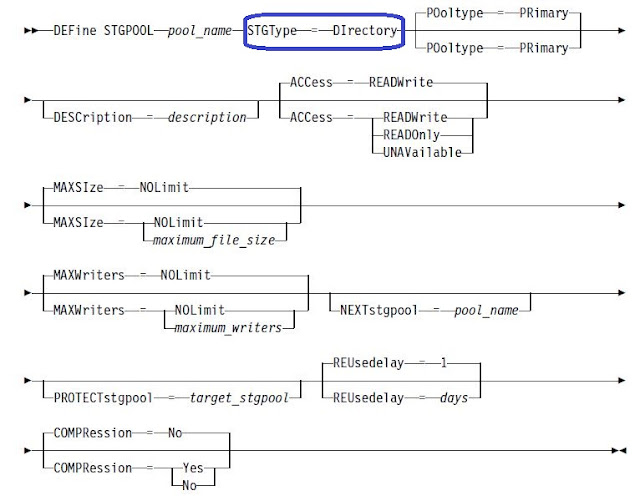
How to define directory container storagepool
Example: define stgpool prod_stg stgtype=directory compression=yes
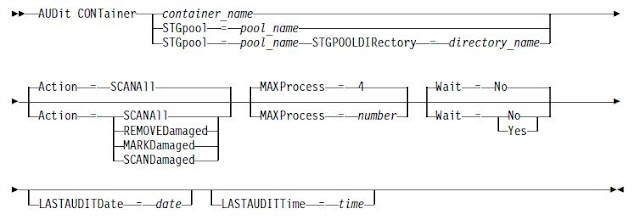
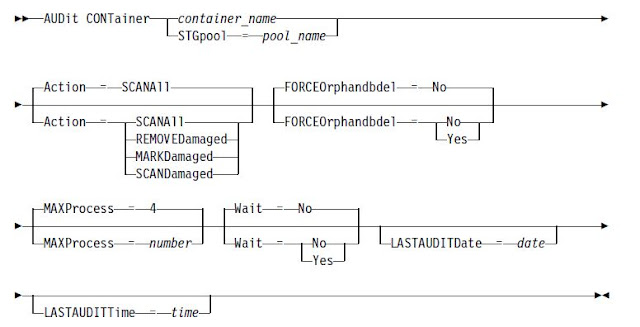
Auditing Directory-Container Storagepools
Use the AUDIT CONTAINER command to scan for inconsistencies between database
information and a container in directory container storage pool.
This command is used to complete the following actions for a container in a directory-container storage pool
- Scan the contents of a container to validate the integrity of the data extents.
- Remove damaged data from a container.
- Mark an entire container as damaged
Example: audit container stgpool=newdedup action=removedamaged