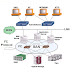
Cristie Tivoli Bare Metal Recovery (TBMR) is a third party software which works together with IBM TSM BAclient software to backup system files and regular data files. When disaster occurs, Cristie TBMR with the help of TSM BAclient can able to restore the data files along with the operating system to its current backup state without the OS CD. Cristie TBMR backs up not only the data files, but the operating systems, applications, networks etc. along with all customizations and configurations as they were before the failure. It actually builds a perfect clone of your entire software infrastructure. TBMR backups can be taken periodically, along with configuration information, which includes details of hard disks, network interfaces, etc. It is possible to recover the original system to the same system or to another system with a dissimilar hardware.
In this post, I will share how to use Cristie TBMR & TSM BAclient to save the system configuration information, backup and recover a Linux machine. TBMR for Linux can be installed on a x86, x86_64 or PPC Linux machine.
Also Read: 11 tips to increase restore performance
Also Read: 11 tips to increase restore performance
Cristie TBMR Limitations
- Platforms other than Intel.
- Multi-boot operating systems
- Recovery of files that are being written to at the time of backup.
How to protect Linux systems using Cristie TBMR and TSM BAclient softwares
1) Install & Configure BA client on the client machine as usual.
2) Install TBMR on the client system you wish to protect.
3) Use the tbmrcfg command to capture and store the configuration of the system.
4) Use the TSM BA Client to backup the data files & system configuration file generated in the above step to your TSM server.
Also Read: Use these Exclude options during backup to save storage pool space
Also Read: Use these Exclude options during backup to save storage pool space
Follow these below steps
- First, the TSM BA client should be configured to backup all files which are required for OS recovery. By default, the /dev directory is not backed up. To make sure this is backed up, the following line should be added to the dsm.sys file: virtualmountpoint /dev
- This will create a separate filespace for /dev which will be restored by the recovery environment.
- To save the system configuration information of the client machine, by default, the following command tbmrcfg is used. It is recommended that this is run prior to running each BA client backup to ensure the configuration is up to date.
- To save configuration information from a machine that boots using grub installed on /dev/sda to the backup location, use:
- To save configuration information from a machine that boots using grub installed on /dev/hda, use:
tbmrcfg -b grub -d /dev/hda
You can also use man tbmrcfg command to check the syntax.
- In order to ensure that you can recover to the latest version of the operating system that was installed on your Linux machine, you must ensure that a TSM incremental backup is performed every time the operating system files change. You have to run tbmrcfg commnad to generate new updated system configuration information in /TBMRCFG directory, this must be done before the backup is run to make sure that we have the latest system configuration backup along with client data files. The best recommended way is to add preschedulecmd parameter with tbmrcfg in dsm.sys file value as shown below.
- System configuration information is always saved to /TBMRCFG directory, it can't be saved anywhere else. We have to make sure to backup this directory during our regular BA client backups.
How to recover a Linux server using Cristie TBMR and TSM BAclient softwares
Below are the following steps to recover the Linux machine to its current backup state
- Boot into Recovery environment (using ISO file which you have downloaded) and configure as required.
- Read Configuration Data from your backup
- Restore Files from your backup
- Load additional drivers (if necessary)
- Reboot into recovered OS
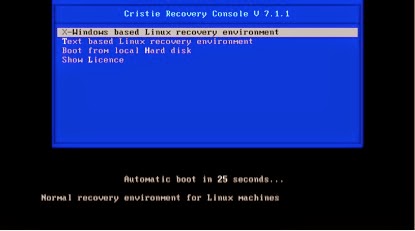
When the client machine is crashed, it can be recovered using the TBMR bootable CD-ROM. This is the same CD from which you have installed the software. You should ensure your machine’s BIOS is set up to boot from CD-ROM. You will see a screen as below.
You can choose which method you want to use for recovering the system, GUI or text based. GUI is the easiest one. If you select the X-window based recovery option, you should see a screen as below.
Here also, you can choose Automatic recovery or Manual Recovery option. Before starting you first need to setup network information in the tools tab. Watch the below video to know how to recover an Linux system to its current backup state using Cristie TBMR.
Note:
- If the machine fails to boot after the restore, you can raise a cristie support request. Cristie support will require copies of the log files to diagnose any problems. Log files has exactly what has happened during the recovery on your system. Without them, it is very difficult to troubleshoot. The Location of log files is /var/log/cristie/recovery/
- In our case, the NIC drivers for the NIC card we are using are not included in the recovery ISO, Cristie can help you to fix this kind of issues, they gave us a new customized recovery ISO file suitable for our environment. So, it is recommended to check the recovery on a test system before implementing on a production server.
- You can download Cristie TBMR trial version software from their website and test it for 30 days. Then you have to update the license information to extend it. Updating license info can be done online from the portal or manually on client system. As of my experience, they gave good customer service.