The type of IP network used is crucial for an iSCSI SAN, as it is absolutely fundamental to performance, security, and availability. A misconfigured network configuration will result lots of issues. Below are the commonly used network options for iSCSI SAN.
Shared IP Network: This is the cheapest, simple and least secure network consideration, it also has less performance. In this network configuration, iSCSI traffic shares the same L2 broadcast domain with all other network traffic. It is suitable for test and development environments but not in the production environment. If the IP network is unstable or very busy, there might be a performance problems.
Dedicated Physical Network: This configuration offers the best in security, performance and availability and is the most common choice in the real time scenarios. As with iSCSI HBA or CNA, if you are deploying a mission critical business applications on an iSCSI SAN then it would be secure enough and best option to choose. It is a cost effective as it requires to buy new set of network infrastructure.
Also Read: Virtualizing Storage to simplify management
Also Read: Virtualizing Storage to simplify management
Dedicated VLAN: Dedicated network connection for the iSCSI traffic on each server offers segregation of iSCSI traffic from other network traffic. This can increase performance and if the VLAN is non-routable, it offers modest levels of security. This option does not require additional costs and also provide performance and security.
Virtual LAN OVerview
Virtual LANs (VLANs) are logical networks created on a LAN. A VLAN enables communication between a group of nodes with a common set of functional requirements independent of their physical location in the network. VLANs are particularly well-suited for iSCSI deployments as they enable isolating the iSCSI traffic from other network traffic (for example, compute-to-compute traffic) when a physical Ethernet network is used to transfer different types of network traffic.
A VLAN conceptually functions in the same way as a VSAN. Each VLAN behaves and is managed as an independent LAN. Two nodes connected to a VLAN can communicate between themselves without routing of frames even if they are in different physical locations. VLAN traffic must be forwarded via a router or OSI Layer-3 switching device when two nodes in different VLANs are communicating even if they are connected to the same physical LAN. Network broadcasts within a VLAN generally do not propagate to nodes that belong to a different VLAN, unless configured to cross a VLAN boundary.
Also Read: Introduction to VSAN
Also Read: Introduction to VSAN
To configure VLANs, an administrator first defines the VLANs on the switches. Each VLAN is identified by a unique 12-bit VLAN ID (as per IEEE 802.1Q standard). The next step is to configure the VLAN membership based on an appropriate technique supported by the switches, such as port-based, MAC-based, protocol-based, IP subnet address-based, and application-based.
- In the port-based technique, membership in a VLAN is defined by assigning a VLAN ID to a switch port. When a node connects to a switch port that belongs to a VLAN, the node becomes a member of that VLAN.
- In the MAC-based technique, the membership in a VLAN is defined on the basis of the MAC address of the node.
- In the protocol-based technique, different VLANs are assigned to different protocols based on the protocol type field found in the OSI Layer 2 header.
- In the IP subnet address-based technique, the VLAN membership is based on the IP subnet address. All the nodes in an IP subnet are members of the same VLAN. In the application-based technique, a specific application, for example, a file transfer protocol (FTP) application can be configured to execute on one VLAN.
VLAN Trunking & Tagging
Similar to the VSAN trunking, network traffic from multiple VLANs may traverse a trunk link. A single network port, called trunk port, is used for sending or receiving traffic from multiple VLANs over a trunk link. Both the sending and the receiving network components must have at least one trunk port configured for all or a subset of the VLANs defined on the network component.
As with VSAN tagging, VLAN has its own tagging mechanism. The tagging is performed by inserting a 4-byte tag field containing 12-bit VLAN ID into the Ethernet frame (as per IEEE 802.1Q standard) before it is transmitted through a trunk link. The receiving network component reads the tag and forwards the frame to the destination port(s) that corresponds to that VLAN ID. The tag is removed once the frame leaves a trunk link to reach a node port.
Also Read: Traditional and Virtual Storage Provisioning Overview
Also Read: Traditional and Virtual Storage Provisioning Overview
Stretched VLANs also allow the movement of virtual machines (VMs) between sites without the need to change their network configurations. This simplifies the creation of high-availability clusters, VM migration, and application and workload mobility across sites.
Link & Switch Aggregation
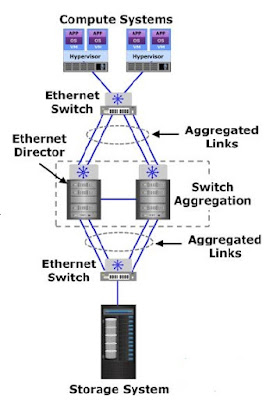
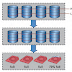
Like an FC environment, the link aggregation in an Ethernet network also combines two or more parallel network links into a single logical link (port-channel). Link aggregation enables obtaining higher throughput than a single link could provide. It also enables distribution of network traffic across the links that ensure even link utilization. If a link in the aggregation is lost, all network traffic on that link is redistributed across the remaining links. Link aggregation can be performed for links between two switches and between a switch and a node. The below figure shows an example of link aggregation between two Ethernet switches. In this example, four links between the switches are aggregated into a single port-channel.
Switch aggregation combines two physical switches to make them appear as a single logical switch. All network links from these physical switches appear as a single logical link. This enables nodes to use a port-channel across two switches. The network traffic is also distributed across all the links in the port-channel. Switch aggregation allows ports in both the switches to be active and to forward network traffic simultaneously. Therefore, it provides more active paths and throughput than a single switch or multiple non-aggregated switches under normal conditions, resulting in improved node performance. With switch aggregation, if one switch in the aggregation fails, network traffic will continue to flow through another switch. In the figure, four physical links to the aggregated switches appear as a single logical link to the third switch.
Self Forming Networks
Self-forming network allows an Ethernet switch to join an Ethernet network automatically. To join an Ethernet network, the new switch is simply powered-up and cabled to an existing switch in the network. The Ethernet network automatically detects the new switch and populates its routing table to start forwarding network traffic immediately.
Self-forming link aggregation enables an Ethernet network to automatically include new interswitch links into a port-channel and redistributes network traffic among all the links in the port-channel. Instead of manually configuring individual links into a port-channel on multiple Ethernet switches, port-channels are automatically formed when new connections (links) are added between the switches. This enables an organization to scale network bandwidth between the Ethernet switches quickly.
Both the self-forming network and the self-forming link aggregation help in meeting the next generation IT demands. They simplify the configuration and ongoing management operations of network infrastructures by automating some of the configuration tasks. They also reduce manual, repetitive, and error-prone network configuration tasks. Further, they provide the agility needed to deploy, scale, and manage the network infrastructure.
Go To >> Index Page
What Others are Reading Now...

0 Comment to "5.4 Network Considerations for iSCSI SAN Deployment"
Post a Comment